Penetration testing project
 Updated 15 Aug Bletchley P op Fiddler - Free cross-platform web debugging proxy with user-friendly companion tools. Spotlight Consultancy services Bespoke services Live online Global delivery Why choose us? NetBootcamp OSINT Tools - Collection of OSINT links and custom Web interfaces to other services such as Facebook Graph Search and various paste sites. Netzob - Reverse engineering, traffic generation and fuzzing of communication protocols. Physical Penetration Testing For IT Security Teams by Wil Allsopp, Advanced Persistent Threat Hacking:
Updated 15 Aug Bletchley P op Fiddler - Free cross-platform web debugging proxy with user-friendly companion tools. Spotlight Consultancy services Bespoke services Live online Global delivery Why choose us? NetBootcamp OSINT Tools - Collection of OSINT links and custom Web interfaces to other services such as Facebook Graph Search and various paste sites. Netzob - Reverse engineering, traffic generation and fuzzing of communication protocols. Physical Penetration Testing For IT Security Teams by Wil Allsopp, Advanced Persistent Threat Hacking:






11 projects tagged "penetration testing"
 Updated 08 Feb creepy P op It is for this exact reason that a genuine penetration test cannot be priced based on the number of IP addresses or number of devices. The audit can be performed through peer review formal audit and should track back to confirm that the issues raised during the audit have been fixed. A pen-tester will reveal how newly discovered threats or emerging vulnerabilities may potentially be assailed by attackers. Organization can face legal issues due to a small loophole left in a software application. How to Price a Penetration Testing Project. It can be easily combined with other tools to provide a powerful command line framework for raw network access.
Updated 08 Feb creepy P op It is for this exact reason that a genuine penetration test cannot be priced based on the number of IP addresses or number of devices. The audit can be performed through peer review formal audit and should track back to confirm that the issues raised during the audit have been fixed. A pen-tester will reveal how newly discovered threats or emerging vulnerabilities may potentially be assailed by attackers. Organization can face legal issues due to a small loophole left in a software application. How to Price a Penetration Testing Project. It can be easily combined with other tools to provide a powerful command line framework for raw network access.


Penetration Testing in a Project- Part 1 | AAJ Technologies
Updated 27 Jan Metasploit Express P op Scan and probe into the ports. What happens if those 10 IP addresses require 1, man-hours of work to test because they are exceedingly complex? See It in Action Divider text here.


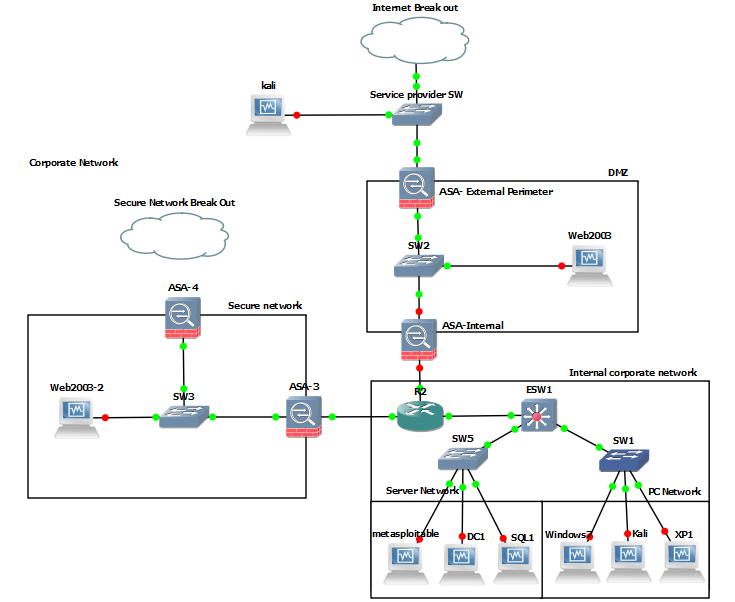


penetration tester

Description: Penetration Tests are valuable for several reasons: By attempting a few weak passwords across a large set of user accounts, user account lockout thresholds can be avoided. This allows your organization to more intelligently prioritize remediation, apply needed security patches and allocate security resources more effectively to ensure that they are available when and where they are needed most. What is Penetration Testing? Steps in Penetration Testing:
Views: 1302
Date: 03.06.2015
Favorited: 5










.jpg)



























User Comments
Post a comment
Comment: