Penetration test method
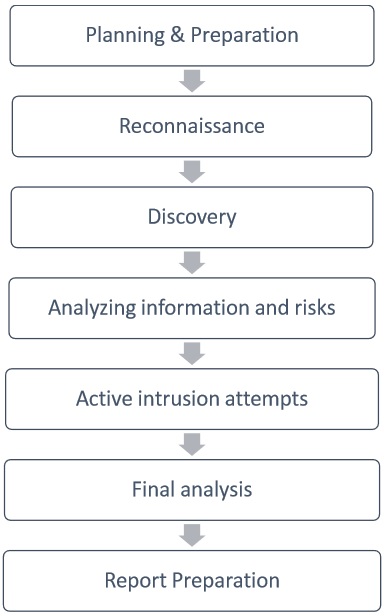
 In this phase, we report the findings in a way that is understandable and acceptable by the organization that owns that system or hardware. No matter how hard the management and IT teams at these businesses try to combat these types of security breaches, the hacker is always one step ahead. Static analysis — Inspecting an application's code to estimate the way it behaves while running. But look at this way: We will never sell your information to third parties. These cover everything related to a penetration test - from the initial communication and reasoning behind a pentest, through the intelligence gathering and threat modeling phases where testers are working behind the scenes in order to get a better understanding of the tested organization, through vulnerability research, exploitation and post exploitation, where the technical security expertise of the testers come to play and combine with the business understanding of the engagement, and finally to the reporting, which captures the entire process, in a manner that makes sense to the customer and provides the most value to it. The penetration testing execution standard consists of seven phases:
In this phase, we report the findings in a way that is understandable and acceptable by the organization that owns that system or hardware. No matter how hard the management and IT teams at these businesses try to combat these types of security breaches, the hacker is always one step ahead. Static analysis — Inspecting an application's code to estimate the way it behaves while running. But look at this way: We will never sell your information to third parties. These cover everything related to a penetration test - from the initial communication and reasoning behind a pentest, through the intelligence gathering and threat modeling phases where testers are working behind the scenes in order to get a better understanding of the tested organization, through vulnerability research, exploitation and post exploitation, where the technical security expertise of the testers come to play and combine with the business understanding of the engagement, and finally to the reporting, which captures the entire process, in a manner that makes sense to the customer and provides the most value to it. The penetration testing execution standard consists of seven phases:

Albina. Age: 28. rien de plus excitant que deux belles femmes disponibles uniquement pour vous, deux belles bisexuelle pour pimenter vos nuits.





Penetration Testing – Complete Guide with Sample Test Cases
 This is a crucial step. It discovers the open, unauthorized and less secured hotspots or Wi-Fi networks and connects through them. We can divide this external approach into two methodologies. External penetration testing When most people think of penetration testing, they usually concentrate on external hackers trying to break into their network. About us Contact us Advertise Testing Services All articles are copyrighted and can not be reproduced without permission. The client and the tester jointly define the goals so that both the parties have the same objectives and understanding. Soils in arid areas, such as the Western United States , may exhibit natural cementation.
This is a crucial step. It discovers the open, unauthorized and less secured hotspots or Wi-Fi networks and connects through them. We can divide this external approach into two methodologies. External penetration testing When most people think of penetration testing, they usually concentrate on external hackers trying to break into their network. About us Contact us Advertise Testing Services All articles are copyrighted and can not be reproduced without permission. The client and the tester jointly define the goals so that both the parties have the same objectives and understanding. Soils in arid areas, such as the Western United States , may exhibit natural cementation.

Luigina. Age: 19. This stimulating opportunity is offered by an attractive , sweet and honest girl with warm caring hands
Standard penetration test - Wikipedia
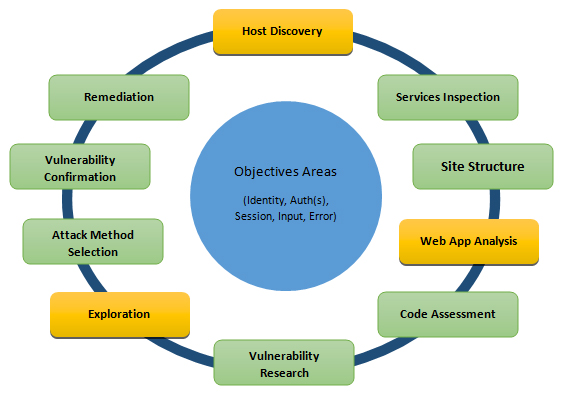
A variety of techniques have been proposed to compensate for the deficiencies of the standard penetration test, including the Cone penetration test , in-situ vane shear tests, and shear wave velocity measurements. Thank You… 22 Ganesh Its a very good info for me, can you please suggest a open source tool for pentesting with examples and how to use it. The data is gathered in order to better plan for your attack. What You Will Learn:






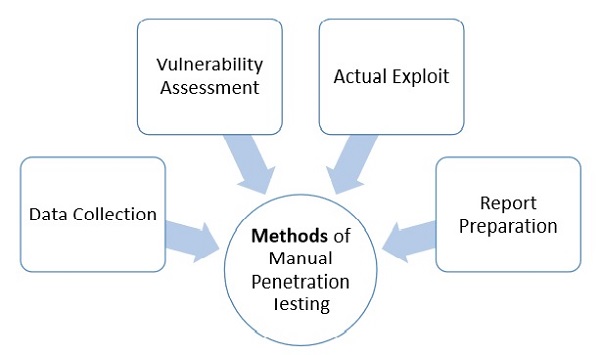
Summarizing The Five Phases of Penetration Testing

Description: Standard Penetration Test blow counts do not represent a simple physical property of the soil, and thus must be correlated to soil properties of interest, such as strength or density. A Firewall can prevent sending data outside the network without your permission. Copyright - Geotechdata. There are many free tools and services available in the market which can give you information like database or table names, DB versions, software versions, hardware used and various third-party plugins used in the target system. Users of this practice are cautioned that compliance with Practice D does not assure reliable testing.
Views: 5012
Date: 16.12.2015
Favorited: 5


































User Comments
Post a comment
Comment: