Penetration testing projects
 What is the work environment and culture like at EY? Build a tool that generates something like this label http: Within this project we research a new attack technique that allows Ten 10 years of project management experience in leading projects. Note - formal education is not mandatory. The information is presented in a map inside the application where all the retrieved data is shown, accompanied with relevant information i.
What is the work environment and culture like at EY? Build a tool that generates something like this label http: Within this project we research a new attack technique that allows Ten 10 years of project management experience in leading projects. Note - formal education is not mandatory. The information is presented in a map inside the application where all the retrieved data is shown, accompanied with relevant information i.






Social engineering penetration testing: Four effective techniques
 If you are already an Arch Linux user, you can setup BlackArch tools collection on top of it. This course serves as comprehensive guide for any network and security professional who is starting a career in ethical hacking and penetration testing. Building an intelligent enterprise: Buckman of Buckman Labs, Dr. Skip to primary navigation Skip to content Skip to primary sidebar Skip to footer. It is the most advanced penetration testing platform out there. Strategy Distinctiveness and Hedge Fund Performance:
If you are already an Arch Linux user, you can setup BlackArch tools collection on top of it. This course serves as comprehensive guide for any network and security professional who is starting a career in ethical hacking and penetration testing. Building an intelligent enterprise: Buckman of Buckman Labs, Dr. Skip to primary navigation Skip to content Skip to primary sidebar Skip to footer. It is the most advanced penetration testing platform out there. Strategy Distinctiveness and Hedge Fund Performance:



Patricia. Age: 19. hello gentlemen, thanks for visiting my page. I'm completely feminine, charming, seductive and unique. I'm a sexy blonde with all natural 38dd boobs, shapely long legs... I'm a perfect female companion any man would want to be seen with on his arm. I promise you that you will experience the very best high class escort service available, as your time spent with me will always be relaxed, spontaneous and authentic and will be a sensually uplifting experience on all levels.
Penetration testing methodologies - OWASP
This was last published in July Designed as a quick reference cheat sheet providing a high level overview of the typical commands you would run when performing a penetration test. Why you need an internal security pen testing program. Command Description upload file c: A good pen tester will always remember to check spelling and grammar; a well-written email, even a short one, will be much more believable.


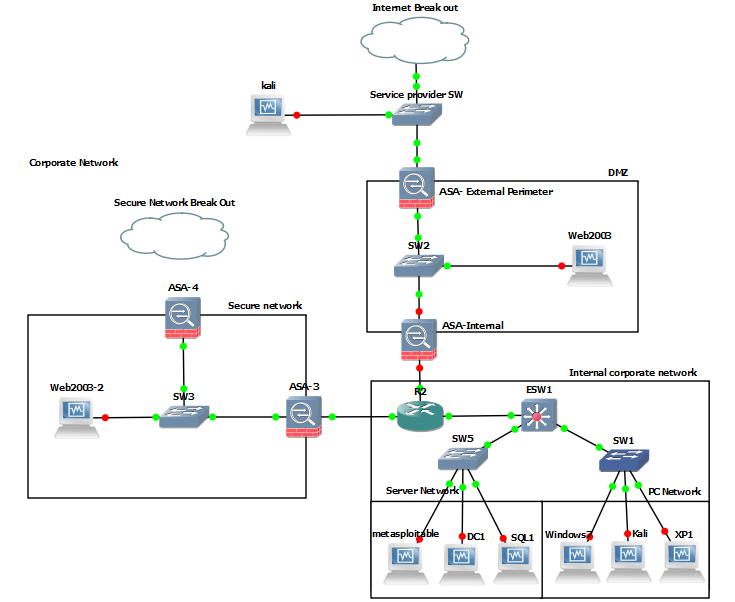



Best Linux Distributions for Hacking and Penetration Testing

Description: Building A Better Pen Tester" - filled with 42 useful tips for becoming a better penetration tester. At Offensive Security, we deliver a quality product tailored to your needs. He has a passion for computer security, finding flaws in mission-critical systems, and designing mitigations to thwart motivated and resourceful adversaries. There are several types of incentives and motivators to which people are highly susceptible, allowing social engineers to persuade people to take an action. X onesixtyone -c names -i hosts SNMP enumeration.
Views: 4495
Date: 18.12.2015
Favorited: 5



































User Comments
Post a comment
Comment: