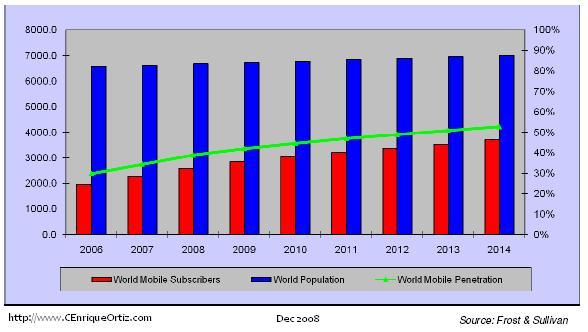
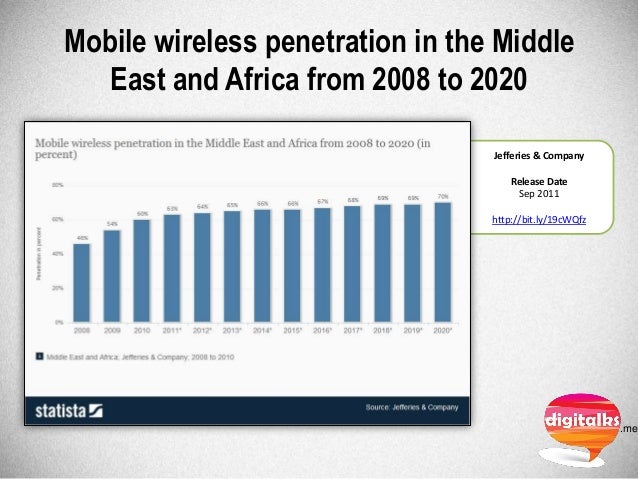
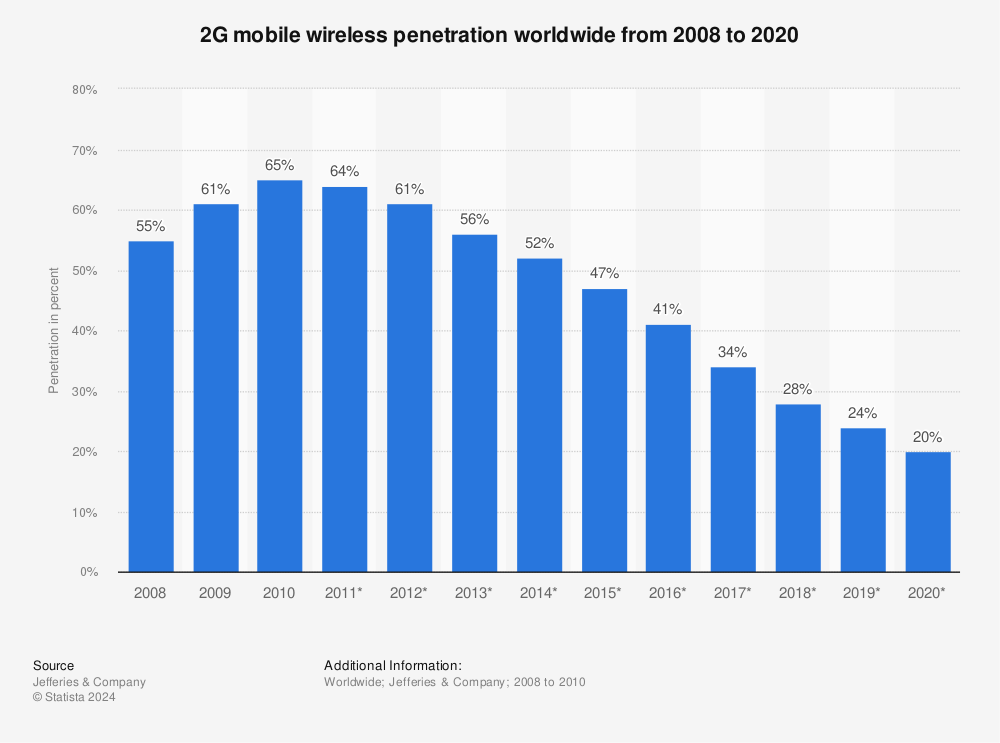
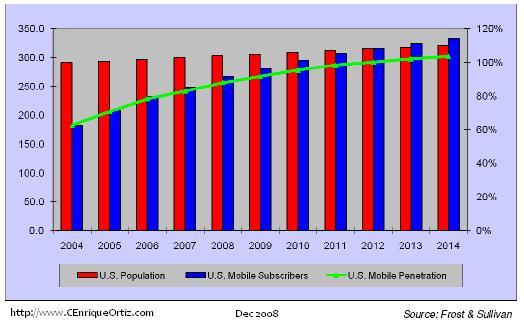
Wireless penetration 2008
 Customized infographic service Presentation Design Animated videos Whitepapers, E-Books, etc. The world is waking up to the environmental impacts caused by plastic waste, and the European Union is declaring war on single-use plastics. Statista for Your Company: This feature is limited to our corporate solutions. Recent Statistics Popular Statistics. Statista offers dossiers and reports on over industries. Our updated in-depth report contains all relevant data and insights and includes an excel file with a detailed list of electric cars, trucks, cargo vehicles, buses, and their specifications.
Customized infographic service Presentation Design Animated videos Whitepapers, E-Books, etc. The world is waking up to the environmental impacts caused by plastic waste, and the European Union is declaring war on single-use plastics. Statista for Your Company: This feature is limited to our corporate solutions. Recent Statistics Popular Statistics. Statista offers dossiers and reports on over industries. Our updated in-depth report contains all relevant data and insights and includes an excel file with a detailed list of electric cars, trucks, cargo vehicles, buses, and their specifications.



Cracking of wireless networks
 Additionally, Loblaw Companies stores sell prepaid feature phones and top-up vouchers. They call someone who breaks into computers an intruder, attacker, or cracker. The -O option instructs Nmap to try to determine the operating systems of the targets. The -sU -sV options instruct Nmap to use application data for application identification. Enterprises with a website or home page, by firm size, 2. Home broadband adoption also varies by age, location, racial and ethnic background, as well as household income, Smith points out. The use of MAC filtering to protect your network will not work as MACs using the network can be easily detected and spoofed.
Additionally, Loblaw Companies stores sell prepaid feature phones and top-up vouchers. They call someone who breaks into computers an intruder, attacker, or cracker. The -O option instructs Nmap to try to determine the operating systems of the targets. The -sU -sV options instruct Nmap to use application data for application identification. Enterprises with a website or home page, by firm size, 2. Home broadband adoption also varies by age, location, racial and ethnic background, as well as household income, Smith points out. The use of MAC filtering to protect your network will not work as MACs using the network can be easily detected and spoofed.


Estelle. Age: 18. My main goal is to give you the time that you are aiming to fulfill, whether it's for your lunch break or your full hour (I aim to Please)
Computer Security Student | Cyber Security Lessons, Tutorials, and Training
Please update this article to reflect recent events or newly available information. Some information on management frames will be helpful to better understand what programs for reconnaissance do. Metasploit is not suited for finding the vulnerabilities of a host; a vulnerability scanner is. Nessus uses plug-ins to find vulnerabilities by sort.
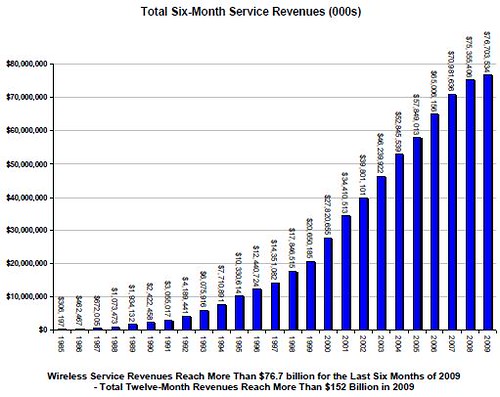





Broadband Portal
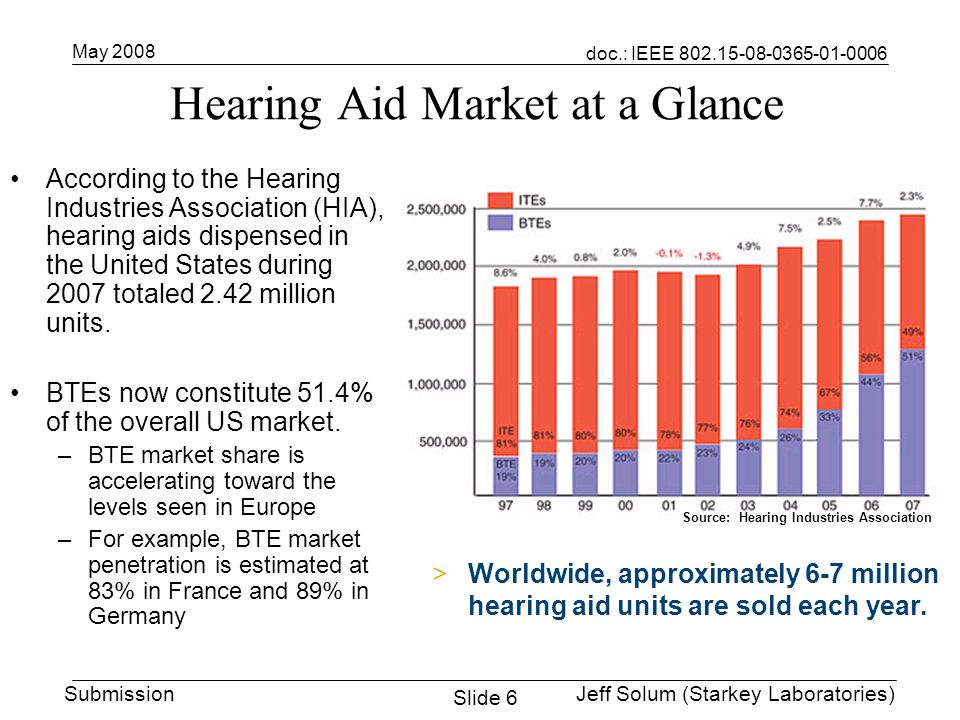
Description: However, like Wireshark, Airopeek requires thorough knowledge of the protocols to use it to its ability. The reference gives a list of Meterpreter commands. In the past, turning off the broadcasting of the SSID has also been thought to give security to a wireless network. The purpose of a back door is to maintain a communication channel and having methods to control a host that has been gained entry to. Currently Being Deployed [14].
Views: 5510
Date: 02.07.2015
Favorited: 5



































User Comments
Post a comment
Comment: